Two days ago Mark Russinovic released a new tool call sysmon in his Sysinternals Suite (which is owned by Microsoft now).
This tool can help you getting an overview about things that often happen on your system while it is or is getting compromised by creating events for specific things like the change a precess creation time, creation of new processes and optionally new network connections into the eventlog.
Here´s an extract of the features from the official website:
Overview of Sysmon Capabilities
Sysmon includes the following capabilities:
-
Logs process creation with full command line for both current and parent processes.
-
Records the hash of process image files using SHA1 (the default), MD5 or SHA256.
-
Includes a process GUID in process create events to allow for correlation of events even when Windows reuses process IDs.
-
Optionally logs network connections, including each connection’s source process, IP addresses, port numbers, hostnames and port names.
-
Detects changes in file creation time to understand when a file was really created. Modification of file create timestamps is a technique commonly used by malware to cover its tracks.
-
Generates events from early in the boot process to capture activity made by even sophisticated kernel-mode malware.
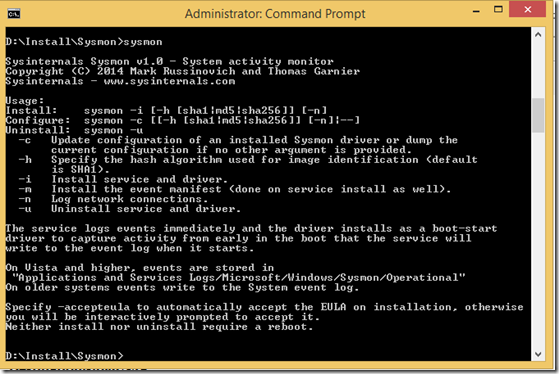
After you downloaded it, extract it and just run sysmon.exe to see the parameters it offers:
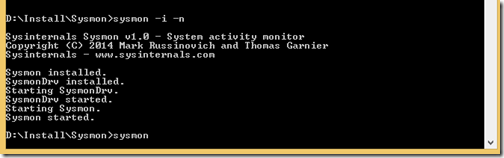
To install sysmon as a service and with network connection monitoring enabled, run
sysmon –i –n
After accepting the EULA it will install and show you the result:
No reboot is needed, the service starts working immediately.
You can now open your Eventviewer and navigate to Applications and ServicesMicrosoftWindowsSysmonOperational (for Windows 8.1) to see the entries:
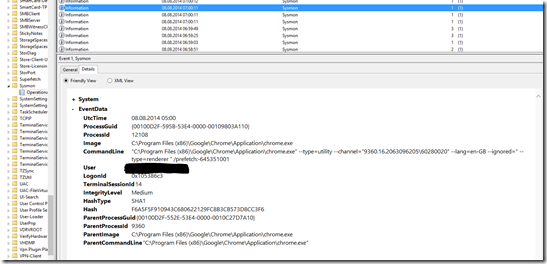
EventID 1 is for a new created process. This is the Details-tab of EventID 1:
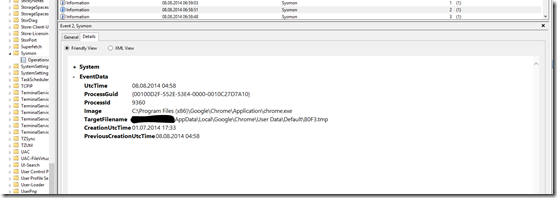
EventID 2 is for changes of a file creaton time:
Like Larry Stelzer in his post about sysmon, I see many entries related to chrome with this EventID.
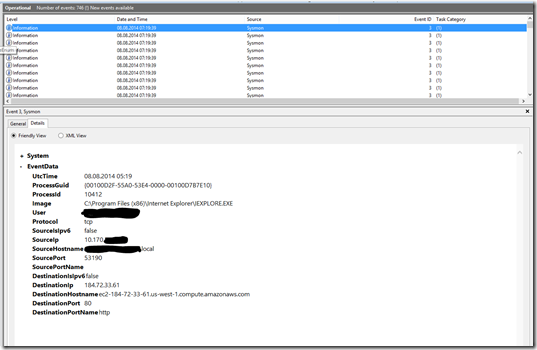
EventID 3 stands for a new network connection:
´
An important note on the official site states:
Note that Sysmon does not provide analysis of the events it generates, nor does it attempt to protect or hide itself from attackers.
So while this tool can help you analyze what was/is going on, it can happen that the log also gets compromised.
But: if your SIEM or Log-server tool of choice gets involved, this new tool can help catching the bad guys earlier.
Sources:
http://technet.microsoft.com/en-us/sysinternals/dn798348
http://www.zdnet.com/sysinternals-new-sysmon-tool-looks-for-intruder-traces-7000032058/